Intrusion detection in a controlled computer network environment using hybridized random forest and long short-term memory algorithms
Keywords:
Intrusion, Detection, Security, HybridAbstract
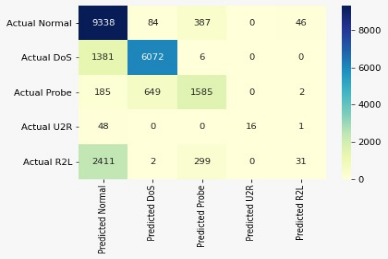
The unending reliant on network access in everything we do, and with the increasing dominance of online communication, there is urgent need to address computer network security challenges now, more than ever. Most of the existing Intrusion Detection Systems (IDSs) struggle to keep pace with the ever-changing characteristics of newly emerging threats. This research proposes a hybrid model that is effective in detecting both majority and minority attack classes using Random Forest (RF) and Long Short-Term Memory (LSTM) algorithms in a controlled computer network environment. Individually, the RF and LSTM models have limitations, but their individual strengths were extracted and subsequently hybridized to cover each other's weaknesses. To handle the challenge of class imbalance, a class weight was applied to the model’s loss function. This approach prompts the model to give extra attention to the minority class attacks. The meta classifier optimized the RF-LSTM combination and offered a more improved model that is effective in detecting both majority and minority classes simultaneously. The hybrid model was analyzed using the Neural Simulator Language- Knowledge Discovery in Databases (NSL-KDD) dataset. The model was deployed in a virtual network environment consisting of three operating systems and a host. The RF – LSTM hybrid model performed exceptionally well by achieving a prediction accuracy of 98.3%, precision of 96.98, recall and F1score of 96.58 and 97,03 respectively, all after 100 epochs at 0.01 learning rate. This outcome addresses shortcomings and lapses hitherto suffered by most intrusion detection models (assessing minority class attacks).
Published
How to Cite
Issue
Section
Copyright (c) 2025 A. I. Bassey, M. A. Agana, E. A. Edim, O. Njama-Abang

This work is licensed under a Creative Commons Attribution 4.0 International License.



